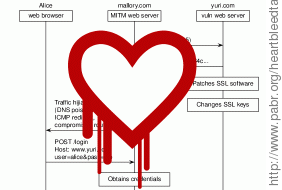
The Heartbleed vulnerability is possibly the worst thing that ever happened to online trust. Ironically, Heartbleed makes HTTPS less secure than plain HTTP because attackers can obtain sensitive data without even having to intercept traffic. For details about the bug itself, see [HEARTBLEED], [CVE-2014-0160] and [XKCD1354].
Initial reactions focused on patching vulnerable web servers, revoking SSL certificates and changing user passwords. It took a couple more days to realize that Heartbleed also affects client software, non-web SSL traffic and countless embedded devices which will never receive a software update.
In the following sections, attack scenarios are illustrated with Message Sequence Charts. See Section 6, “ Acknowledgements ” for LaTeX source code examples.
Following an old tradition of cryptographic literature, character names are associated with archetypal roles:
Alice, Bob: Users of online services.
Eve: A passive attacker (eavesdropper).
Trudy: An active attacker who may exploit the Heartbleed bug by sending specially crafted heartbeat packets over an SSL (e.g. HTTPS) connection.
yuri.com: A web site with vulnerable SSL software.
Since OpenSSL is so widely used, any web site should be considered as a potential yuri.com until proven otherwise.
george.com: A web site with unaffected or patched SSL software.
All prominent web sites are probably safe at the time of writing, but thousands of minor sites will probably never comment on the issue, leaving their users wondering. If you have doubts about your favorite web site, try [LASTPASS]. You can also check manually whether the site certificate has a NotBefore date posterior to 7 April 2014. This is a good indication that they have dealt with Heartbleed (although this may yield both false positives and false negatives because a site can renew an expired certificate without changing the keys, and also replace the keys without affecting the dates). As a last resort, [FILIPPO] lets you test whether a web server is still vulnerable. Warning: This service will "attack" any server on your behalf, which might bring legal trouble.
Victor: A user with vulnerable SSL software.
To determine whether you are in Victor's shoes rather than Alice's, check your version of the OpenSSL and/or libSSL packages. Versions 1.0.1 through 1.0.1f are vulnerable (except when compiled with non-default options). According to [ARS_CLIENTS], Android 4.1.1 is affected. If you are unsure, see [REVERSEHEARTBLEED]. Warning: Do not send the malicious URLs to anyone.
mallory.com: A malicious server which may impersonate web sites or attack vulnerable SSL clients.
brad.com: A host which serves content for prominent web sites, such as advertisements, static resources, web beacons, Javascript libraries, CSS stylesheets, multimedia files.
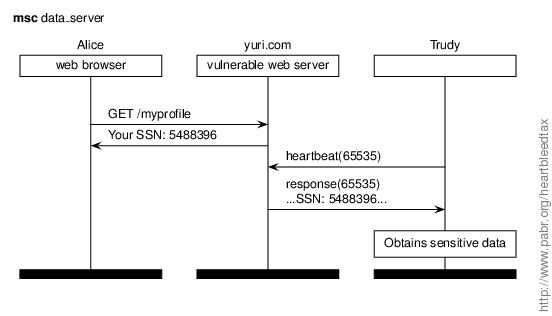
In this scenario Alice enters or consults sensitive data on yuri.com over HTTPS. Plain-text data linger in the memory of the web server. Later, Trudy connects as a regular HTTPS clients and exploits Heartbleed.
Countermeasures for end users.
- Do not exchange sensitive information with a web site until they tell you they have dealt with Heartbleed.
Field reports.
- Canadian charged in 'Heartbleed' attack on tax agency (reuters.com)
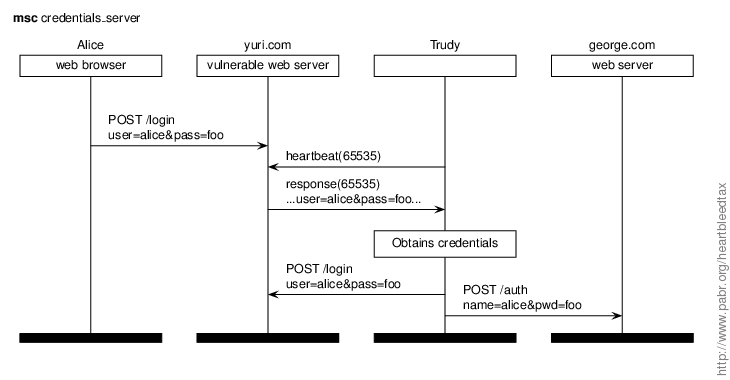
In this scenario Alice authenticates with yuri.com by supplying a login and password over HTTPS. Later, Trudy connects as a regular HTTPS clients and exploits Heartbleed to extract these credentials. Trudy can then access Alice's accounts on yuri.com and on any other web site where she used the same username and password.
Countermeasures for end users.
- Do not enter your password on a web site until they tell you they have dealt with Heartbleed.
- Afterward, change your password.
- In the meantime, beware of phishing attempts, e.g. emails which invite you to come and change your password on a fake web site.
Lessons learned.
- Never use the same password on several web sites.
- Use multi-factor authentication.
- Use SSL mutual authentication (client-side certificates) ?
Field reports.
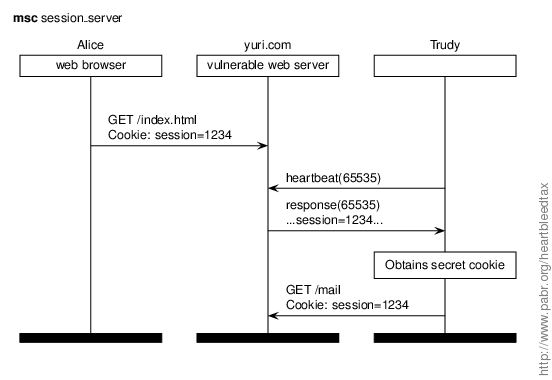
In this scenario Trudy extracts session cookies rather than login credentials. This allows her to take control of Alice's account without waiting for her to enter her credentials.
Countermeasures for end users.
- Log out of online services until they have dealt with Heartbleed.
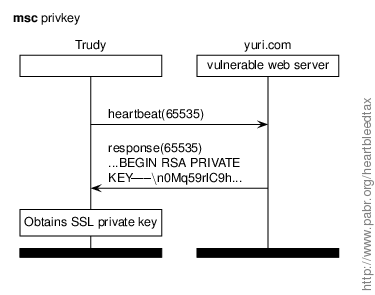
In this scenario Trudy extracts the SSL/TLS private key of yuri.com. Regardless of what happens next (see below), leakage of private keys is always a major failure.
Lessons learned.
- Protect private keys with a hardware security module.
Field reports.
- Confirmed: Heartbleed Exposes Web Server's Private SSL Keys (securityweek.com)
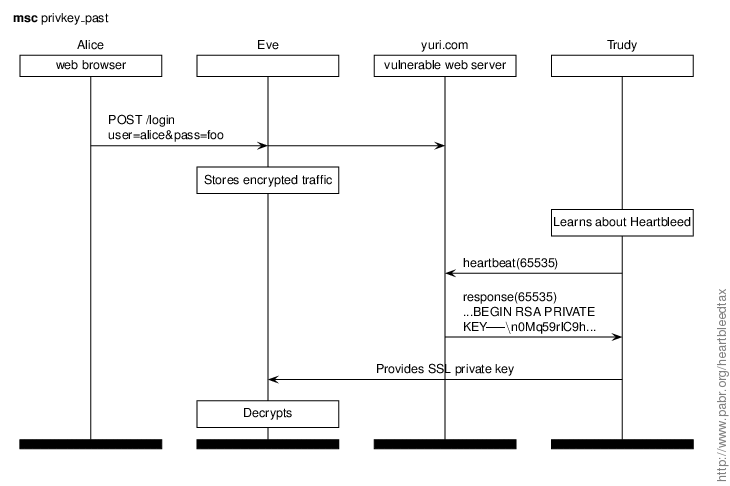
In this scenario Trudy extracts the SSL private key of yuri.com and uses it to decrypt traffic that was previously intercepted by Eve, possible before the Heartbleed bug was even introduced in OpenSSL.
Here comes the return on investment for those entities which are in the business of archiving petabytes of encrypted traffic !
Lessons learned.
- Use perfect forward secrecy.
- Change key pairs regularly.
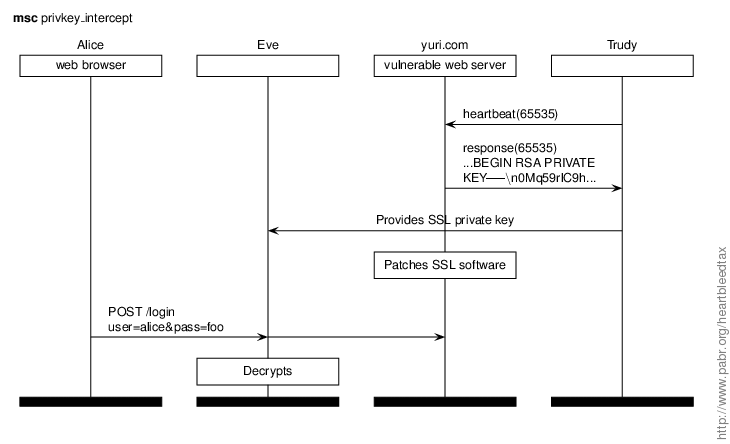
In this scenario Trudy extracts the SSL private key of yuri.com and uses it to decrypt traffic, even after yuri.com has patched its SSL software.
Countermeasures for end users.
Check that affected web sites have either changed their keys or certified that the keys were never at risk.
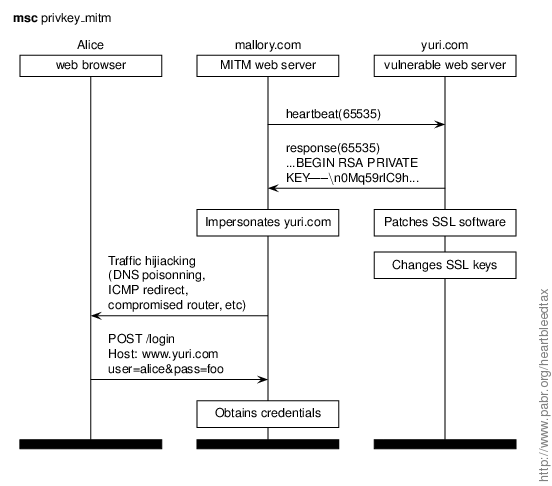
In this scenario mallory.com impersonates yuri.com after extracting its SSL private key. This so-called man-in-the-middle attack (MITM) is more dangerous than passive snooping because mallory.com can trick Alice into using a compromised certificate. It also allows mallory.com to defeat some multi-factor security measures.
Countermeasures for end users.
- Check whether your browser detects revoked certificates: [REVOKED_GRC].
- If it does not, inspect certificates manually.
Lessons learned.
- Heartbleed will probably be the end of the current certificate revocation infrastructure. [LANGLEY] explains the problem and mentions alternatives such as OCSP stapling and DNSSEC.
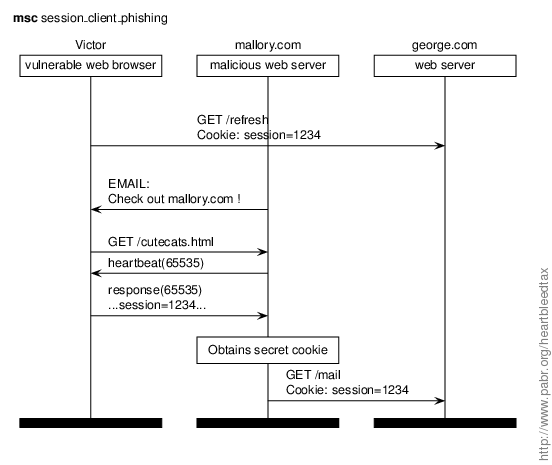
In this scenario mallory.com extracts data from Victor, a client with vulnerable SSL software.
Countermeasures for users.
- Upgrade your browser software.
- Use distinct user accounts or browser instances for casual web surfing and for secure transactions.
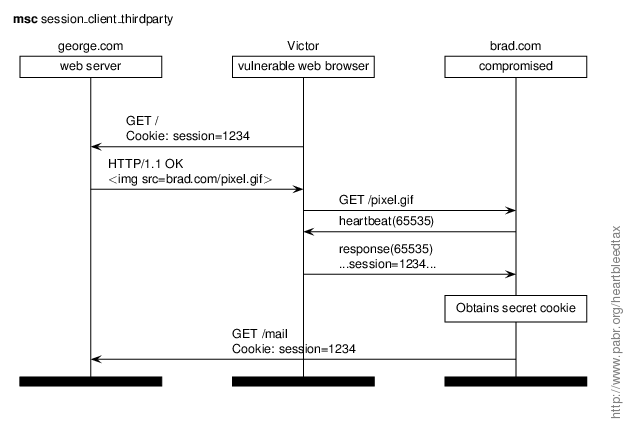
In this scenario Trudy takes control of brad.com, one of many providers which serve web resources for george.com. Victor is attacked even though he believed he was only connecting to george.com, whom he trusts.
Countermeasures for users.
- Upgrade your browser software.
- Block third-party content.
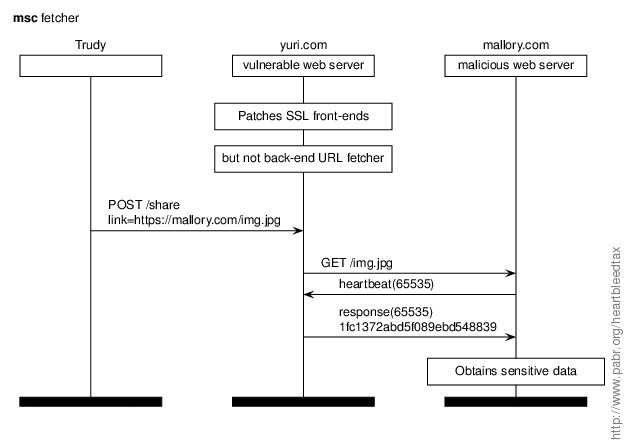
Here Trudy tricks yuri.com into retrieving a URL from mallory.com, which uses that opportunity to extract data from a vulnerable back-end server of yuri.com. This scenario affects web crawlers, social networks which pre-render links shared by users, page translation services, HTML compliance testers, etc. However, it is still unclear whether any sensitive data would leak.
Lessons learned.
- Back-end machines deserve as much care as web front-ends.
Field reports.
- Testing for "reverse" Heartbleed - What did we find ? (meldium.com)
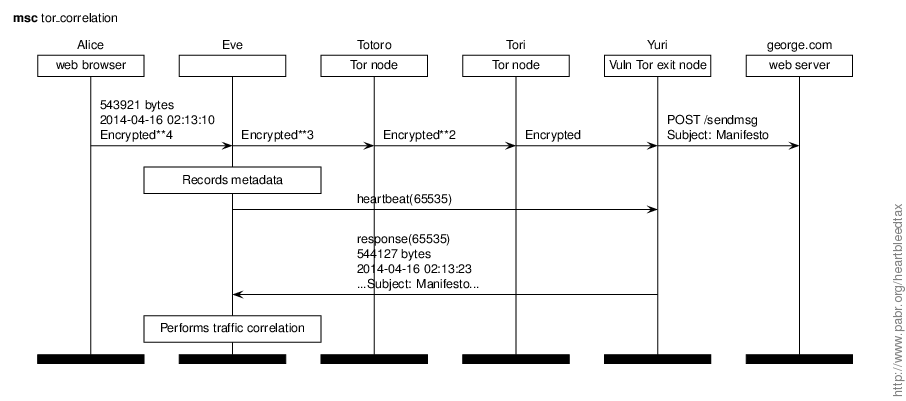
Eve, an evil dictator, wants to establish that Alice is using Tor to communicate with george.com, a foreign human-rights organization. Eve can spy on all Internet traffic within her national boundaries but has no wiretapping authority in other countries. She exploits Heartbleed massively against vulnerable Tor exit nodes in order to match outgoing traffic with her local intercepts.
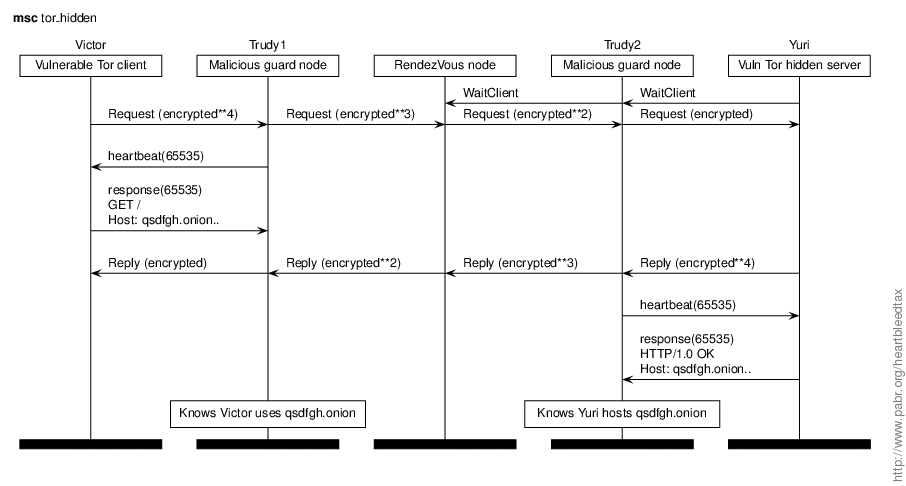
Trudy sets up a number of malicious Tor guard node. She exploits the Heartbleed vulnerability against clients that connects to them, including Tor hidden servers and their users. Although Tor hidden services are encrypted end-to-end, Trudy can identify vulnerable users and servers based on plaintext data leaked by Heartbleed at each end. Besides, if she extracts the private key of a hidden service, she can impersonate it.
Field reports.
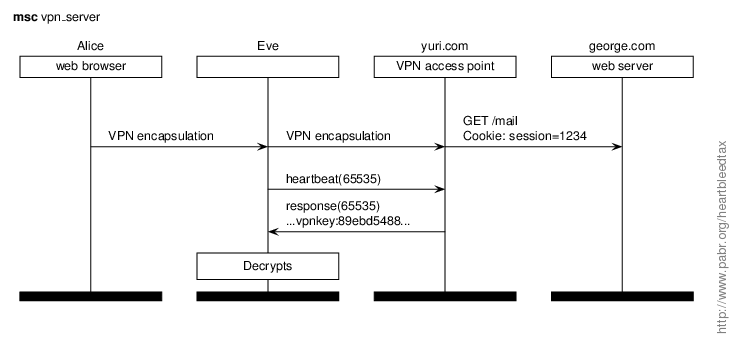
Alice is aware that most public WiFi networks provide no privacy. Therefore she has configured her smartphone and laptop to connect to the Internet through a VPN service provider, yuri.com. (Alternatively, she could be running her own VPN server at home, or using the VPN feature that comes bundled with her DSL modem or her NAS box.) Eve snoops on the WiFi network that Alice is currently using, notices SSL-based VPN traffic from her smartphone, exploits Heartbleed against the destination IP address, and retrieves either VPN keys or plaintext traffic.
Field reports.
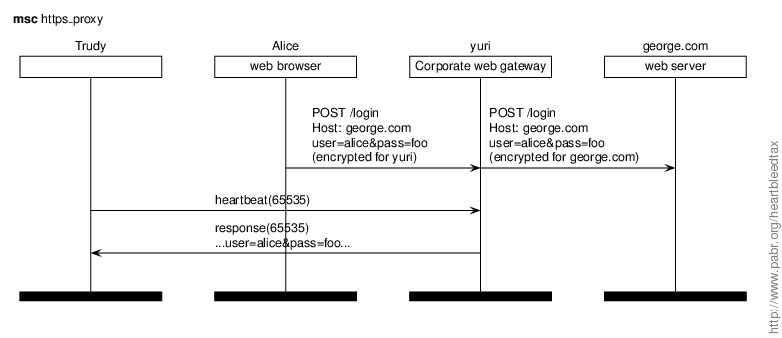
Alice does online banking from her work computer. She has checked that her bank's website, george.com, is not affected by Heartbleed. However, her employer routes outgoing web traffic through yuri, a web gateway which enforces acceptable use policies and scans for malware. To inspect HTTPS traffic, yuri acts as a certification authority trusted by Alice's browser (it will generate a certificate on the fly for george.com). Trudy, a co-worker of Alice, exploits Heartbleed against the proxy and extracts sensitive information.
Countermeasures for end users.
- Do not exchange sensitive information with a web site until your IT department has dealt with Heartbleed.
Lessons learned.
- The chain of trust is only as strong as its weakest link.
Field reports.
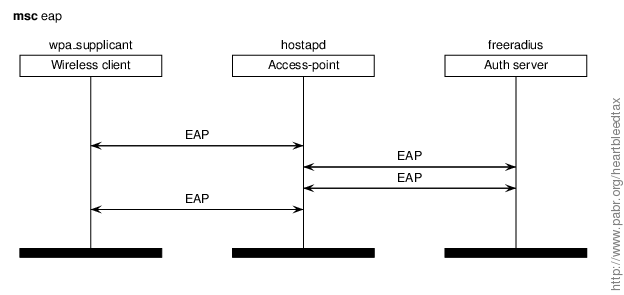
Enterprise networks typically rely on EAP variants which provide stronger security than the PSK mode used in home networks. The EAP-PEAP, EAP-TLS and EAP-TTLS standards happen to use TLS messages (like HTTPS, except not over TCP). Popular implementations (wpa_supplicant, hostapd, and freeradius) are based on OpenSSL and may therefore be vulnerable to Heartbleed.
Scenarios.
- Malicious client extracts server certificate from vulnerable AP, then uses it to decrypt traffic.
- Fake AP extracts credentials from vulnerable client, then uses them to connect to the real AP.
In configurations where the AP delegates authentication to a central server, insiders may also attack the server itself.
Note that EAP is used not only in wireless networks, but also for port-based network access control in wired ethernet (IEEE 802.1X).
Field reports.
Besides HTTPS, several SSL/TLS-based services and protocols might turn out to be affected by Heartbleed:
- Online trusted timestamping and notarization services, where private keys are used for signature rather than privacy
- Automatic software update infrastructures.
- RADIUS, Diameter and similar security protocols, when used over TLS.
- SMTPS, POP3S, IMAPS.
- SIPS.
- Electronic currency protocols and wallet applications.
- Open-source development infrastructures and source code repositories (git).
- Online voting systems.
Hopefully the Heartbleed fiasco will educate users about online security and stimulate progress, such as:
- Research in secure yet efficient programming languages.
- Revamping the whole X509 certification infrastructure so that client software has no excuse to accept revoked certificates.
Message Sequence Charts are rendered with [MSCSTY]. Here is an expanded LaTeX source code example: credentials_server_example.tex
[HEARTBLEED] The Heartbleed Bug . http://heartbleed.com.
[CVE-2014-0160] CVE-2014-0160. https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160.
[XKCD1354] How the Heartbleed bug works . http://xkcd.com/1354/.
[FILIPPO] Heartbleed Test . https://filippo.io/Heartbleed/.
[LASTPASS] LastPass Heartbleed checker . https://lastpass.com/heartbleed/.
[REVOKED_GRC] Security Certificate Revocation Awareness Test . https://revoked.grc.com/.
[ARS_CLIENTS] Vicious Heartbleed bug bites millions of Android phones, other devices . http://arstechnica.com/security/2014/04/vicious-heartbleed-bug-bites-millions-of-android-phones-other-devices/.
[REVERSEHEARTBLEED] Reverse Heartbleed Tester . https://reverseheartbleed.com/.
[CUPID] Heartbleed, Cupid and Wireless . http://www.sysvalue.com/en/heartbleed-cupid-wireless/.
[LANGLEY] No, don't enable revocation checking . https://www.imperialviolet.org/2014/04/19/revchecking.html.
[MSCSTY] Drawing Message Sequence Charts with LaTeX . http://satoss.uni.lu/software/mscpackage/.